题目内容
B
Typing your password or credit card number into a computer is a moment’s work. But if you think your personal details disappear as soon as you hit the Return key, think again: they can sit on the computer’s hard disk for years waiting for a hacker to rip them off.
As people spend more time on the web and hackers become more sophisticated, the dangers of storing personal information on computers are growing by the day, security experts say. There are some safeguards, such as never allowing your computer to store your passwords. But even that is no guarantee of security.
When you type in a password, it is stored in random access memory (RAM), where it is held temporarily until other data overwrites it or the computer is switched off.
But every so often, the computer copies the contents of its RAM onto hard disk, where it is easy prey for a hacker, who can read it directly or design a worm to e-mail it back. The longer sensitive data stays in RAM, the more likely it is to be copied onto the disk, where it stays until it is overwritten—which might not happen for years.
Tal Garfinkel and colleagues from Stanford University have created a software tool which simulates the workings of a complete computer system. Within the simulation, sensitive data can be tagged and then tracked as it passes through the system. Next, Garfinkel and his team simulated computers running common software that regularly handles passwords or confidential personal information, such as Internet Explorer, the Windows login script and Apache server software.
In a paper to be presented, they conclude that the programs took virtually no measures to limit the length of time the information is retained. Some of the tested software even copied the sensitive information, apparently without restraint.
This is the first time anyone has tried to measure the extent of this problem, says Rebecca Wright, a security expert at Stevens Institute of Technology. Garfinkel hopes the results will arouse software developers to take action.
40.Which of the following statements is true according to the passage?
A.It is secure to use your password as long as you hit the Return key.
B.Your personal details is likely to be in danger if you spend more time on the web.
C.Your password will be safe if you have some safeguards.
D.Never allowing your computer to store your passwords will be safe.
41.Which of the following is NOT the reason for the unsafety of a password?
A.It will be stored in RAM.
B.It will be copied onto hard disk.
C.It might not be overwritten.
D.It will disappear as soon as you hit the return key.
42.Tal Garfinkel and his team measured the extent of security of .
A.simulating the working of a complete computer system
B.tagging sensitive data
C.passing through the system
D.running common software
43 What can be inferred from the passage?
A.The length of the time the information is stored is not limited.
B.The programs can not retain the information.
C.The security problem should be paid more attention to.
D.Some sensitive information has been copied.
【小题1】B
【小题2】D
【小题3】A
【小题4】C

完形填空
A couple from Minneapolis, in the north, decided to go to Florida, in the south, for a long weekend during one particularly icy cold winter. They both had jobs, and had 1 managing their travel schedules(日程安排)It was decided the husband would fly to Florida on a Thursday, and his wife would 2 him the next day. Upon arriving as 3 , the husband checked into the 4 There he decided to 5 his laptop(computer)and send his wife an email back in Minneapolis. However, he 6 left off one letter in her 7 and sent the e-mail without 8 his error.
In the 9 in Houston, a widow(寡妇)had just returned from her husband’s burial service He was a minister of many years who had been“called home to glory”following a heart 10 (died and gone to report in heaven). The widow checked her e-mail, 1l messages from family and friends. Upon 12 the first message, she was so shocked as to fall to the floor, The widow’s son 13 into the room, found his mother on the floor and saw the computer 14 which read:
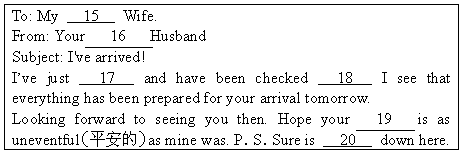
|
(1)A.confidence |
B.argument |
C.doubt |
D.difficulty |
|
(2)A.visit |
B.detect |
C.follow |
D.track |
|
(3)A.aimed |
B.planned |
C.meant |
D.programmed |
|
(4)A.hotel |
B.office |
C.airport |
D.station |
|
(5)A.open |
B.set |
C.show |
D.begin |
|
(6)A.willingly |
B.accidentally |
C.purposely |
D.aimlessly |
|
(7)A.article |
B.sentence |
C.address |
D.letter |
|
(8)A.looking |
B.watching out |
C.noticing |
D.observing |
|
(9)A.absence |
B.course |
C.meantime |
D.case |
|
(10)A.blow |
B.knock |
C.strike |
D.attack |
|
(11)A.hearing |
B.typing |
C.hoping |
D.expecting |
|
(12)A.taking |
B.reading |
C.staring |
D.bringing |
|
(13)A.rushed |
B.charged |
C.hurried |
D.walked |
|
(14)A.screen |
B.keyboard |
C.window |
D.mouse |
|
(15)A.Living |
B.Loving |
C.Brave |
D.Poor |
|
(16)A.Disappeared |
B.Deserted |
C.Departed |
D.Dead |
|
(17)A.gone |
B.died |
C.left |
D.arrived |
|
(18)A.over |
B.back |
C.out |
D.in |
|
(19)A.arrangement |
B.journey |
C.voyage |
D.adventure |
|
(20)A.hot |
B.sad |
C.new |
D.quiet |
Family members of Rebiya Kadeer have asked her not to organize violence or undermine (破坏) the peaceful life in Xinjiang, in letters made public on Monday. They blamed her for organizing the riot in Urumqi on July 5 and apologized to the victims in two separate letters.
Kadeer’s son Khahar, daughter Roxingul and younger brother Memet wrote a letter to her, expressing their discontent for her turning against her own promises of not taking part in separatist activities and voicing their anger over the violent event.
“Because of you, so many innocent people lost their lives in Urumqi on July 5, and so many houses, shops and vehicles were burnt or damaged," they wrote. "The harmony and unity among ethnic groups were undermined."
Xinjiang is a happy home to people of different ethnic groups and no one wants to destroy it, they wrote. “We want a stable and safe life,” they said. “Please think about the happiness of us and your grandchildren. Don't destroy our happy life here. Don’t follow the provocation (挑衅) from some people in other countries.”
In another letter to the victims of the July 5 riot, they held Kadeer and the World Uygur Congress (WUC) responsible for the riot. “Evidence proved the riot was organized by the WUC, led by Rebiya Kadeer, and carried on by a group of separatists within the Chinese borders.”
After an incident between Uygur and Han workers of a factory in Shaoguan of southern Guangdong Province broke out on June 26, Kadeer exaggerated (夸大) the facts on the Internet, raising the death toll from two to more than 50, and posted false pictures, which started the violent event, they wrote.
“Those who committed crimes should take the responsibilities,” they said.
The statement from the Urumqi Public Security Bureau said the 319 people had been detained (拘留) after information was received from the public or obtained through the police investigation.
The arrests are in addition to the 253 detentions, police announced on July 29. Before that, more than 1,000 suspects had been detained by July 6, the second day of the violence.The suspects would face charges in connection with the riot that left 197 people dead.
"Every suspect, without any exception, will be arrested and punished according to the law to root out any hidden danger,” it said.
1.All the following are correct according to the passage EXCEPT “_________”.
A. The riot took place on July 5 B. WUC organized the riot
C. The riot left 197 people dead D. Khahar was injured in the riot
2.The letter to Kadeer was written to__________.
A. show how the incident happened B. express their sorrow over the riot
C. blame Kadeer for her wrong doing D. tell the story of Kadeer
3.How many suspects have been detained according to the passage?
A. About 1252 B. Above 1572 C. About 1319 D. 1197
4.From the passage we learn that_________.
A. the riot caused great loss to the people in Urumqi
B. WUC was responsible for the incident in Shaoguan
C. most of the suspects will be sentenced to death
D. Kadeer voiced her a pology over the July 5 riot
##Begin#
|
TOSHIBA ELEVATORS LTD is one of the leading elevator companies in the world with more than 120 branch companies around the globe. SHENYANG TOSHIBA ELEVATORS LTD in Shenyang produces high-quality elevators. We are offering the following positions: ● Plant Manager Excellent Senior Engineer with experience in this field to manage our plant in Shenyang ● Senior Engineers (Mechanical and Electrical) For production and Engineering Department, good command of Internet ● Junior positions For those who wish for success ● One purchaser (购货员) Preferably with experience in a mechanical engineering company and international markets ● Cost Accountant (会计) 5 years experience in mechanical factory costing, good knowledge in Office 2000, CET level. For these senior level Positions, we expect preferably a university degree or an excellent job record. 3-5 years of experience on the job and good command of English. If you are ready to work with us, we will offer attractive salary packet and bright future. SHENYANG TOSHIBA ELEVATORS LTD Shenyang (024-82846556) Liaoning Province |
|
TOWER DAIRY PRODUCT COMPANY LTD is a well-known food company in Suzhou. We’re offering the following positions: (1) Secretary ● University graduate ● Good at English speaking, writing&translating ● Good PC knowledge and typing skill ● Pleasant character with good personal skill (2) Accountants ● College or university graduate ● Good command of English and PC operation ● Work experience (3) Production Trainees ● College or university graduate ● Food engineering/machinery or chemistry ● Good command of English ● 1-2 years experience in food factory ● Leadership ability and PC knowledge (4) Production workers ● Polytechnic (工艺的) school graduate ● Food technology or chemistry ● Knowledge of basic English ●1-2 years experience in food factory TOWER DAIRY PRODUCT COMPANY LTD Suzhou (0512-86734157) Jiangsu Province |
5.If you want to get a senior position in TOSHIBA, you need to have _________.
A. work experience on the job B. typing skills and know English well
C. good wishes for the job D. pleasant character and PC skill
6.Each position offered by TOWER requires the applicant to __________.
A. have work experience B. be a university graduate
C. have good PC knowledge D. have knowledge of English
7.If you don’t know how to use a computer, you had better ask for the position of ________.
A. a secretary in TOWER B. a production worker in TOWER
C. a senior engineer in TOSHIBA D. a cost accountant in TOSHIBA
8.As a graduate from university this year, you can probably get a job as _______.
A. a cost accountant in TOSHIBA B. a purchaser in TOSHIBA
C. a secretary in TOWER D. an accountant in TOWER